Fenvra Insights
Explore the latest trends, news, and information across various topics.
Wireless Wonderland: Exploring the Unseen World of Connectivity
Dive into the magic of wireless technology! Discover hidden connections and innovative trends shaping our connected world today.
The Hidden Infrastructure: How Wireless Signals Travel Through the Air
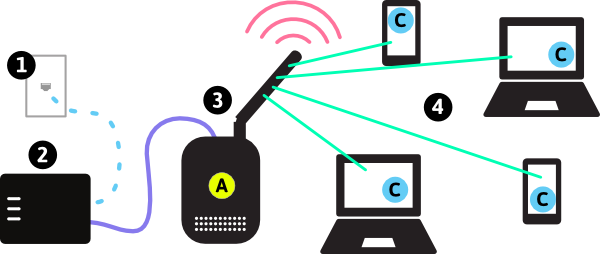
The hidden infrastructure of wireless communication is an intricate system that allows signals to travel seamlessly through the air. At its core, this infrastructure comprises a network of transmitters and receivers that continuously communicate using radio waves. These radio waves are a form of electromagnetic radiation that can traverse vast distances, making it possible for your smartphone to connect to the internet or for you to enjoy uninterrupted streaming. The propagation of these signals is influenced by various factors, including frequency, obstacles, and atmospheric conditions, highlighting the sophistication of this unseen network.
In addition to transmitters and receivers, several technological components play a critical role in ensuring the efficient transmission of wireless signals.
- Cell towers: These structures serve as critical hubs, relaying signals between devices and the core network.
- Repeaters: Used to amplify weak signals, repeaters extend the coverage of wireless networks.
- Frequencies: Different frequencies have unique characteristics that can impact signal quality and range.
Counter-Strike is a highly popular tactical first-person shooter game that has captivated millions of players worldwide since its inception. The game pits teams of terrorists against counter-terrorists in various objective-based scenarios, requiring teamwork and strategy for success. For gamers looking to enhance their mobile experience, checking out the Top 10 Samsung Galaxy S Accessories can provide valuable insights into the best equipment to use while playing on the go.
Decoding Wireless Technology: What You Need to Know About Connectivity
Wireless technology has rapidly transformed the way we connect and communicate in our daily lives. From smartphones to smart homes, understanding the underlying principles of connectivity is crucial for anyone looking to keep up with the evolving digital landscape. At its core, wireless technology relies on electromagnetic waves to transmit data over distances, enabling devices to interact without physical connections. Key components include routers, modems, and various frequency bands, each playing a critical role in ensuring seamless communication. Familiarizing yourself with terms like Wi-Fi, Bluetooth, and 5G will enhance your ability to navigate and select the best connectivity options available.
As we delve deeper into wireless technology, it's important to recognize the challenges that come with it. Issues such as signal interference, limited range, and security vulnerabilities can affect connectivity. To mitigate these, consider following best practices like optimizing router placement, utilizing strong encryption methods, and regularly updating device firmware. By prioritizing these aspects, you can ensure a more reliable and secure connection. Understanding the intricacies of connectivity not only enriches your knowledge but also empowers you to make informed decisions that enhance your digital experience.
What Are the Benefits and Risks of a Wireless-Connected World?
In today's digital age, the transition to a wireless-connected world offers numerous benefits that can significantly improve our daily lives. One of the primary advantages is the enhanced convenience of staying connected anytime and anywhere. Wireless technologies, such as 5G and Wi-Fi 6, enable faster data transmission and seamless communication across devices. Additionally, the accessibility of information has expanded exponentially; people can access educational resources, news, and social networks with just a few taps on their smartphones. Moreover, industries benefit from increased efficiency as wireless solutions facilitate remote work, improve collaboration, and streamline operations.
However, this wireless-connected world does come with its share of risks. Security vulnerabilities are a major concern, as hackers can exploit weak networks to gain unauthorized access to personal data. Cybersecurity threats, such as data breaches and identity theft, pose significant risks to businesses and individuals alike. Furthermore, the rapid deployment of wireless technologies can lead to issues related to privacy infringement and digital surveillance, impacting users' autonomy. It is essential to strike a balance between harnessing the advantages of wireless connectivity while implementing robust security measures to mitigate associated risks.